Cybhermetics®
Cy-bher-met-ics
The science of designing, implementing, and maintaining an airtight cyber security solution.
Cyber – Relating to or characteristic of the culture of computers, information technology and virtual reality.
Hermetics – Complete and airtight.
Implementing a world-class security solution goes well beyond technology. Organizations must also understand the complexities of human nature as well as rapidly changing cultural and generational nuances. With the proliferation of cloud technologies, the boundaries between your organization’s network and the public sphere have become almost indiscernible. As a result, cybersecurity is an ever-evolving endeavor that doesn’t end by simply installing the latest antivirus update. At Moruga, cybersecurity isn’t simply a product or service, it’s a comprehensive philosophy. Over 90% of security breaches are the result of human error. Cybhermetics is an exhaustive security methodology fusing the latest security technology with the psychology of impulsive behavioral patterns.
Cybhermetics consists of the following 5 elements:
- Compliance
- Access Solutions
- Intelligence
- Endpoint Security
- Video Surveillance
Cybhermetics Compliance
Whether your industry has specific security compliance requirements or not, maintaining documented security policies and computer network configurations is imperative. In addition, ensuring that your employees are educated on the latest cybersecurity threats is more important than ever. Moruga’s Cybhermetics Compliance ensures your organization’s managed security policies and documentation are always accurate and up to date. We also provide your employees with security awareness training to ensure they understand the extent of the latest threats they are facing. Employees are tested regularly, often unbeknownst to them, to ensure they are constantly mindful of organizational security.
![]() Corporate Security Policy and Documentation
Corporate Security Policy and Documentation
![]() Cyber Security Awareness Training
Cyber Security Awareness Training
![]() Vulnerability Assessments
Vulnerability Assessments
![]() Compliance Certification
Compliance Certification
![]() Cyber Liability Insurance
Cyber Liability Insurance
Cybhermetics Access Solutions
Access solutions such as IPsec VPN, SSL VPN, etc. are still widely used throughout the industry to provide secure access to private networks. With the adaptation of cloud technologies, the lines between your private network and the public world have become increasingly blurred. New technologies have been created to help keep pace with the security challenges associated with a rapidly evolving cloud landscape. Solutions such as software defined perimeters, zero trust security, network access control (NAC), along with identity and access management, are necessary to reinforce the safety of your organization’s data and computer networks. Moruga routinely assists organizations with these technologies ensuring users can access the data and applications necessary to complete tasks in a safe and productive manner.
![]() Next Generation Firewall Solutions
Next Generation Firewall Solutions
![]() Traditional VPN Solutions
Traditional VPN Solutions
![]() Software Defined Perimeter (Next Gen VPN) – Zero Trust Security
Software Defined Perimeter (Next Gen VPN) – Zero Trust Security
![]() Identity and Access Management Solutions
Identity and Access Management Solutions
![]() Network Access Control (NAC)
Network Access Control (NAC)
Cybhermetics Intelligence
The adage of 100% security equals 0% productivity remains true. This means that allowing your network to communicate with that of another organization (email, web pages, etc.) may put your organization at risk. Sometimes attacks are obvious but often you are not aware of the attack for hours, days or even weeks. Having the technology in place to monitor and log all your network connectivity and security information has become mandatory. Monitoring and logging this information is a great first step but knowing when and how to act on it is equally critical. A comprehensive SIEM (Security information and event management), Cyber Security AI (artificial intelligence), and SOC (security operations center) enables your organization to respond in near real-time to events ensuring minimal disruption or catastrophic damages.
![]() Monitoring and Alert Management
Monitoring and Alert Management
![]() Network Device Logging
Network Device Logging
![]() SIEM (Security Information and Event Management)
SIEM (Security Information and Event Management)
![]() Cyber Security AI
Cyber Security AI
![]() SOC (Security Operation Center)
SOC (Security Operation Center)
Cybhermetics Endpoint Security
Most cyber security attacks originate on endpoint devices located within a secure network. Security awareness training and edge or software defined edge security can only do so much to protect your devices from the modern threats. Having quality endpoint security solutions is imperative. Traditional AV, combined with EDR (endpoint detection and response) and email security help ensure your end points are protected and do not pose a threat to the devices they communicate with.
![]() Antivirus and EDR/MDR/XDR
Antivirus and EDR/MDR/XDR
![]() Email Security
Email Security
Zero Day Protection Suite™
Moruga’s Zero Day Protection Suite™ is a cybersecurity application bundle engineered to protect your endpoint devices from cyberthreats. Deploying these applications together creates the greatest barrier against known and unknown threats ensuring that both your data and network operations are safe and function with limited interruption. The Zero Day Protection Suite™ includes:
Antivirus
Antivirus applications are designed to detect and purge viruses and other types of malicious software from your computers, laptops, and mobile devices. Malicious software, known as malware, is designed to corrupt your devices and compromise your data. Traditional antivirus products use signature-based libraries of known threats designed to detect and purge those threats before damaging the local device and/or infecting other devices.
The Antivirus application in the Zero Day Protection Suite™ is Bitdefender. Bitdefender is a global leader in cybersecurity and its Antivirus platform is consistently rated among the best Antivirus technologies in the industry.
Behavioral Security
Behavioral Security is an artificial intelligence-based application. Behavioral Security tools learn the “normal” patterns of your systems and applications and block activity that deviates from those patterns. Malware, viruses, etc. are not “normal” behaviors, thus Behavioral Security tools prevent malicious code from executing. Behavioral Security functions like a firewall around each application by defining how the application (or file) is permitted to function.
The Behavioral Security application in the Zero Day Protection Suite™ is ThreatLocker®. With a reputation as one of the best Behavioral Security tools available, ThreatLocker® enables you to dictate what is acceptable while blocking everything else. ThreatLocker® provides the following protection points:
- Zero Trust Security
Zero Trust Security delivers a unified approach to protect users, devices, and infrastructure against the exploitation of zero-day vulnerabilities.
- Allowlisting
Application Allowlisting prohibits any application from running that is not explicitly permitted. This means suspicious software such as Malware and Ransomware will be denied by default.
- Ringfencing™
Ringfencing™ controls application permissions including how applications interact with one another. By limiting software functionality ThreatLocker® reduces the likelihood of a successful exploit and prevents the weaponization of legitimate tools such as PowerShell.
- Elevation Control
Elevation Control enables users to run specific applications as a local administrator, even without local admin privileges. Elevation Control enables IT Administrators to dictate exactly what applications can run without giving local admin rights to each individual user.
- Storage Control
Storage Control provides policy-driven control over storage devices, whether the storage device is a local folder, a network share, or external storage such as USB drives. ThreatLocker® Storage Control allows policies to be set which may be as simple as blocking USB drives or as complex as blocking access to your backup share, except when accessed by your backup application.
Browser Security
Browser Security protects endpoints devices against corruption by quarantining all URLs until they have been vetted and proven safe. When users click on a link Browser Security will analyze the domain to ensure the user is not directed to malicious software. Browser Security upscales any chromium-based browser into a secure browser.
The Browser Security included in the Zero Day Protection Suite™ is ConcealBrowse from Conceal. In today’s global environment the internet is a ubiquitous part of everyday business operations. Around-the-clock internet use means that cyberthreats have become omnipresent. Simply clicking a link in an email can reveal information about your organization, and opening a file can be disastrous as it creates an ingress pathway to your network. ConcealBrowse is your frontline browser defense.
Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR), also known as Endpoint Detection and Threat Response (EDTR), is an endpoint security solution that continuously monitors end-user devices to detect and respond to cyberthreats like ransomware and malware. Unlike antivirus software that uses signature-based libraries to detect and remove threats, EDR products focus on collecting data from the endpoint and examining that data for malicious patterns in real-time. This artificial intelligence (AI) driven protection is also referred to as a Next Generation Antivirus and protects against threats unknown to traditional antivirus applications.
The EDR solution included in the Zero Day Protection Suite™ is Singularity Complete by Sentinel One. Considered a pioneer in the EDR industry, Sentinel One is consistently rated among the top EDR solutions on the market.
Security Awareness Training
No cybersecurity solution is complete without comprehensive training. Security Awareness Training educates employees about the potential risks and cyberthreats to applications, networks, and devices. Security Awareness Training heightens each employee’s understanding of their own roles in cybersecurity by educating them on the potential consequences of even seemingly innocuous actions.
The Zero Day Protection Suite™ includes Powered Cybersecurity Training from Stickley on Security (SoS). This SoS training curriculum is designed to address the challenges businesses face as they deploy and manage cybersecurity. You and your leadership team will be empowered to determine everything from quarterly employee education to monthly phishing campaigns designed to identify internal threat vectors. Automated reports will keep you informed of which employees are following your cybersecurity policies and who may need additional training.
Security Policy and Documentation Templates
Creating and maintaining Security Policies and Documentation can be overwhelming and businesses often fail to prioritize this critical element of robust cybersecurity. As part of the Zero Day Protection Suite™, Moruga provides customers with templates to simplify this documentation. Moruga also includes up to 2 hours of additional consulting to ensure all documentation questions are addressed.
Vulnerability Assessment
Vulnerability Assessments identify and classify vulnerabilities in network infrastructures, computer systems, and applications. A vulnerability is a security weakness that could expose the organization to cyberthreats. The Vulnerability Assessment utilizes a network security scanner to audit each device within your network environment. An annual internal and external vulnerability assessment will be completed for all customers using the Zero Day Protection Suite™. A Vulnerability Assessment report will be provided detailing the results of the security audit. Recurring vulnerability scans and remediations (vulnerability management) are available upon request for an additional cost.
Pricing
Base price:
Month to Month – $15 per device
1 Year Commitment – $13.50 per device
3 Year Commitment – $12 per device
Price if M365 is migrated to Moruga
Month to Month – $14 per device
1 Year Commitment – $12 per device
3 Year Commitment – $10 per device
*Volume discounts can also apply
Video Surveillance Systems
Zero Trust networking is a security model that forces all devices and applications to self-identify before they are trusted. This is applicable to people as well. Video surveillance systems that can perform advanced functions such as facial recognition to ensure threats like disgruntled ex-employees and sex offenders are not allowed on-premises, that can detect elevated body temperatures and/or facial masks during pandemics, and that have built-in AI to alert of abnormalities are an increasing necessity to businesses. In addition, ensuring video feeds are constantly monitored eliminates the likelihood such events are missed. Moruga can design, deploy, and manage all of your video surveillance components.
![]() Video Surveillance Systems
Video Surveillance Systems
Your domain is an essential part of your brand. Protect your employees and Customers by preventing cybercriminals
from using your domain in their spear phishing and typosquatting attacks.
How We Crush Spear Phishing and Typosquatting
• Screen Scrape Protection (detects if your website is copied to a domain to attack your Customers)
• Iframe Attack Protection (prevents your website from being pulled to another domain via an iframe)
• Monitor all lookalike domains to prevent spear phishing attacks on staff and Customers
• Monitor typo-domains to prevent typosquatting attacks on your Customers
• Detects any domain using your domain as a subdomain (example: yourdomain.superscam.com)
• Monitors all similar domains that contain “yourdomain” to prevent spear phishing attacks using the unlimited extensions
available (example: usffcu.mobi)
• Monitors DNS including MX records of all lookalike, typo and similar domains to detect if a harmless domain turns malicious
• Take down services for all lookalike, typo and similar domains that are found to be malicious
• DA Prevent Option: Purchase lookalike and typo domains and forward them to primary domain so they cannot be used to attack
your organization
Spear Phishing Prevention
People who receive an email with a domain that looks almost identical to your domain are far more likely to believe the
email is legitimate and trust the link or attachment. According to the 2019 Verizon Data Breach Investigation Report,
92% of all malware infections begin with a phishing email. Locking down all the domains similar to yours is the best way
to prevent them from ever being used for nefarious reasons.
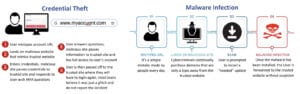
Typosquatting is a Top Source of Credential Theft and Malware Infection
For as long as companies have been registering domain names, cybercriminals and competitors have been using this
tactic to commit a wide range of scams. The two most common scams are tricking a user into downloading malware and
to stealing a user’s credential when they believe they’re logging into your site.
Impersonation attacks can look like any company associated with yours. Some are larger
than others, making them even a better threat. The Domain Assure Ecosystem links your
company with other companies to create the largest protection network possible.
Protect your company from phishing emails impersonating partners, vendors, clients, and big
brands. Partners employees regularly work with are a higher threat as a trusted relationship.
In 2021 86% of companies were compromised by an impersonation attack.